Last Updated on September 25, 2024
The Necro Trojan highlights ongoing security risks in mobile applications, even those found in official app stores. Always exercise caution and verify the integrity of applications before downloading.
Overview of the Necro Trojan
Security researchers have identified a dangerous malware strain known as the Necro Trojan. This malware has infiltrated two legitimate apps on the Google Play Store and several unofficial modified app versions. The Trojan can log keystrokes, steal sensitive information, and install additional malicious software.
Infected Apps on Google Play
The affected apps include:
- Wuta Camera – A photo editing app with over 10 million downloads.
- Max Browser – A web browser with around 1 million downloads.
Kaspersky researchers found the Necro Trojan in versions of these apps prior to updates that removed the malware. Users are urged to uninstall Max Browser immediately, as it remains compromised.
How the Malware Spread
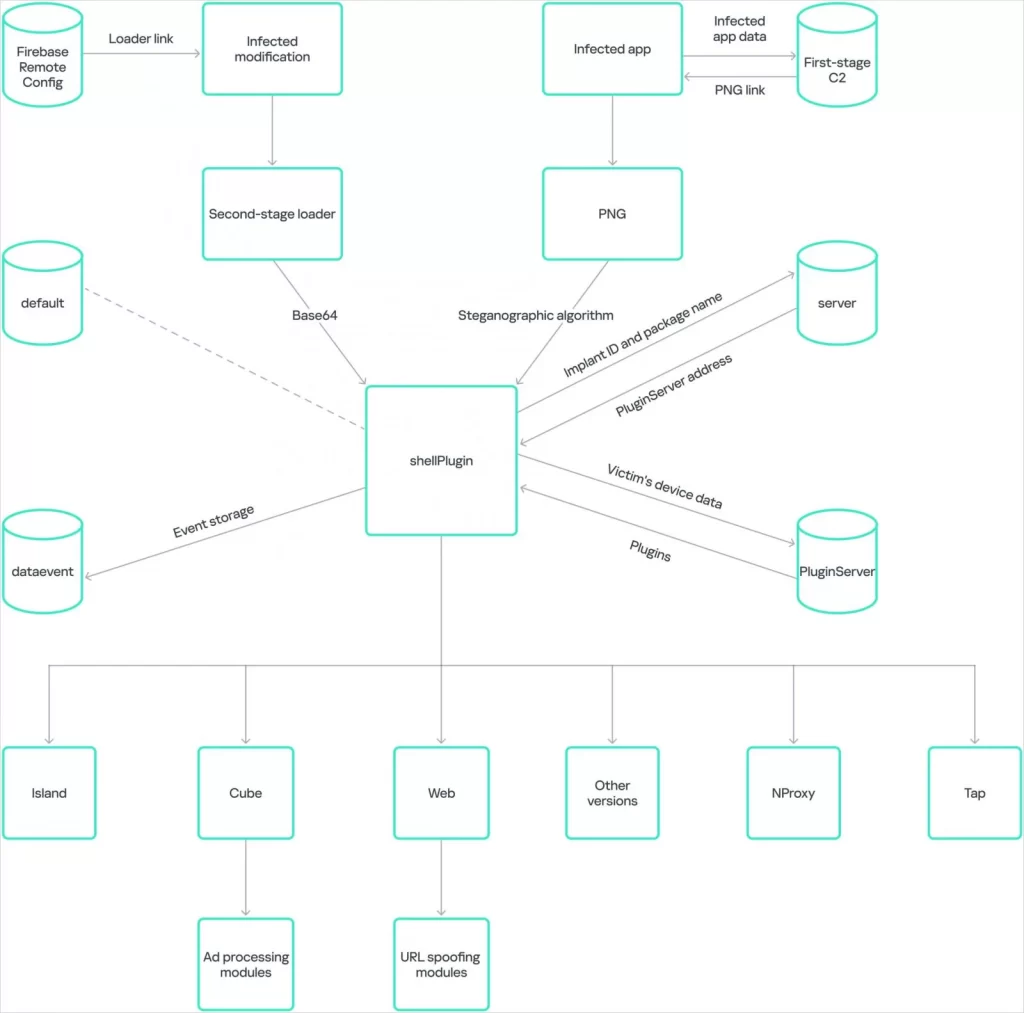
The Necro Trojan spread via a malicious advertising SDK called Coral SDK. This SDK utilized steganography to hide its malicious payload within seemingly harmless images. Users who interacted with these images unwittingly triggered the malware.
Risks from Modified Apps
The threat is not limited to official apps. Numerous modified versions of popular applications have also been found to distribute the Necro Trojan. Notable examples include:
- WhatsApp Mods: GBWhatsApp and FMWhatsApp
- Spotify Mod: Spotify Plus
- Games: Minecraft, Stumble Guys, Car Parking Multiplayer
These modified apps often promise enhanced features or free premium services, making them attractive to users.
Precautions for Users
Users should be cautious when downloading apps from third-party sites. If an app isn’t from a trusted source, it’s best to avoid it. Check download numbers, ratings, and reviews for any app before installation.
Google has sent BleepingComputer the following comment:
“All of the malicious versions of the apps identified by this report were removed from Google Play prior to report publication. Android users are automatically protected against known versions of this malware by Google Play Protect, which is on by default on Android devices with Google Play Services. Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play.” – A Google Spokesperson